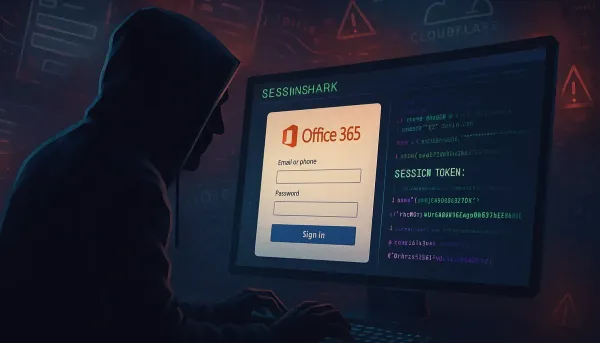
SessionShark- Bypassing MFA Threats in Office 365 Security
In the evolving cyber threat landscape, phishing attacks remain a prevalent method employed by threat actors to compromise sensitive credentials and gain unauthorized access to systems. The recent emergence of the SessionShark phishing kit positions it as a notable player in this domain, particularly targeting Microsoft Office 365 accounts. This toolkit has the troubling capability to bypass multi-factor authentication (MFA) by stealing session tokens, thereby rendering one of the most robust security measures ineffective. This blog post delves into the mechanisms employed by SessionShark, its implications for cybersecurity, and best practices for defending against such sophisticated threats.
Understanding SessionShark
What is SessionShark?
SessionShark is marketed as a phishing-as-a-service (PhaaS) toolkit that targets Microsoft Office 365, explicitly designed to bypass MFA protections. Researchers from SlashNext have detailed that SessionShark utilizes an adversary-in-the-middle (AiTM) approach, enabling it to intercept both login credentials and session tokens. The implications of this are significant: once attackers capture a user’s session token, they can access the victim’s account without needing the additional one-time passcode typically required by MFA.
Mechanism of the Attack
Upon a victim’s attempt to log into Office 365 through a deceptive landing page mimicking the legitimate interface, SessionShark captures the entered credentials and session cookie in real-time. The incorporation of Telegram for immediate alerting allows attackers to exploit stolen credentials almost instantaneously, maximizing the prospect of account takeover before victims can recognize a compromise.
Figure 1: Representation of the attack flow with SessionShark.
User -> Phishing Page (SessionShark) -> Captured Credentials and Tokens -> Attacker via Telegram
Integration with Cloudflare
SessionShark benefitting from Cloudflare’s infrastructure adds another layer of difficulty for cybersecurity teams aiming to track or incapacitate these phishing operations. The ability for SessionShark to operate behind Cloudflare’s protective services effectively masks the real location of the site, complicating detection and takedown efforts.
Evolving Landscape of Phishing Kits
Market Dynamics: PhaaS
The commodification of cybercrime is evident as tools like SessionShark are offered on underground forums, positing themselves as educational tools under the guise of ethical hacking. This emerging PhaaS model mirrors trends seen in ransomware-as-a-service (RaaS), delineating an ecosystem where even inexperienced cybercriminals can launch sophisticated attacks with commercially available kits, thereby lowering the barrier to entry dramatically.
Detection and Evasion Techniques
SessionShark employs several advanced evasion tactics:
- Antibot Technology: Implementing techniques to thwart automated scanners, including presenting CAPTCHA challenges.
- Custom Scripts and Headers: These allow attackers to modify their phishing kits dynamically, making them adaptable to detection patterns from security technologies.
- Near-Perfect Mimicry: The phishing pages created by SessionShark can dynamically adjust in real-time to mirror legitimate login pages closely, increasing the likelihood of victim engagement.
Mitigating Risks and Recommendations
Proactive Defense Strategies
- User Awareness and Training: Continuous education on recognizing phishing attempts is vital. Regular training sessions should include practical scenarios to help staff identify indicators of phishing.
- Security Technology: Organizations should invest in AI-driven security solutions that analyze behavioral patterns and identify anomalies beyond traditional signature-based methods. Tools that leverage machine learning can provide a robust defense against evolving phishing tactics.
- Regular Audits: Routine assessments of login procedures and access controls can help identify vulnerabilities in systems susceptible to tactics employed by phishing kits like SessionShark.
- Reporting Mechanisms: Establish clear channels for reporting suspicious emails or login attempts to promptly address potential phishing incidents.
Recommendations for End Users
- Always verify the URL before entering credentials. Ensure that the address begins with
httpsand belongs to the expected domain. - Enable MFA where possible, regardless of prevalence, and utilize methods that involve a trusted device rather than SMS where feasible.
- Use a password manager to create unique, complex passwords for different services, thereby minimizing risk in case of credential theft.
Conclusion
The advent of the SessionShark phishing kit underscores a critical shift towards more sophisticated phishing tactics that evade traditional security measures, especially targeting MFA. As attackers continue to innovate their methodologies, it becomes imperative for both organizations and individuals to adapt their defenses accordingly. By fostering a culture of cybersecurity awareness and leveraging advanced security technologies, stakeholders can enhance their resilience against such prevalent and evolving threats.
Additional Resources
As the cybersecurity landscape continues to evolve, keeping abreast of the latest threat intelligence and adaptive countermeasures is critical for maintaining robust defenses against emerging cyber threats.